Search results for tag #security
Notepad++'s update servers have been compromised by Chinese hackers and all users had been exposed to malware. The developer estimated the overall compromise period spanned from June through December 2, 2025.
Users should update to version 8.9.1 (or superior) immediately.
Source: https://notepad-plus-plus.org/news/hijacked-incident-info-update/
#security #vulnerability #windows #text #editor #notepad #foss #freesoftware #software
OpenBSD 7.8 // HTTPD // ERRATA 013
Date: February 2, 2026
Name: 013_httpd.patch
Description: Fix a use-after-free in httpd(8) when using chunked encoding.
Link: https://cdn.openbsd.org/pub/OpenBSD/patches/7.8/common/013_httpd.patch.sig
RE: https://mastodon.social/@anthroposamu/116002240561460787
Notepad++ Hijacked by State-Sponsored Hackers
Lort, the "Schroeder's cat" of upgrading. "Our domain was compromised and hijacked by a state-sponsored group from June 2025 until Dec 2025, redirecting Notepad++ update traffic to malicious servers ... Please download this upgrade from our website" #Notepad #Ssoftware #Security #InfoSec
Notepad++ Hijacked by State-Sponsored Hackers
https://notepad-plus-plus.org/news/hijacked-incident-info-update/
<quote>
I deeply apologize to all users affected by this hijacking. I recommand downloading v8.9.1 (which includes the relevant security enhancement) and running the installer to update your Notepad++ manually.
</quote>
#software #security #offrehacked
Notepad++ Hijacked by State-Sponsored Hackers
https://notepad-plus-plus.org/news/hijacked-incident-info-update/
<quote>
I deeply apologize to all users affected by this hijacking. I recommand downloading v8.9.1 (which includes the relevant security enhancement) and running the installer to update your Notepad++ manually.
</quote>
#software #security #offrehacked
New details about the FBI's raid on Washington Post reporter Hannah Natanson's home have come out in government court filings--including details about what devices agents seized.
Incredibly--agents compelled Natanson to unlock one of her MacBook computers using her fingerprint.
This raid demonstrates the problems with biometrics--and what some courts are getting wrong about them. Read about it here:
https://decentproject.org/an-fbi-raid-on-a-reporters-home-shows-the-problem-with-biometrics
🗓️ 2024‑11‑08 • #Android #Privacy #Security
Here’s a quick showdown if you’re thinking of leaving proprietary Android behind:
Murena / e‑OS (Fairphone 4):
Price: €449‑€499
CPU: Snapdragon 750G (≈ 1.9 k Geekbench multi) – decent but slower
GPU: Adreno 619 (≈ 1.1 TFLOPS)
RAM/Storage: 6 / 8 GB RAM, UFS 2.1
Security: Standard verified boot, no dedicated security chip
Updates: Depends on LineageOS – often lagging behind Google’s patches
Pros: Modular, repair‑friendly, microG gives partial Play‑Services compatibility
Graphene OS on Pixal 7: (You could use any Pixal phone from the 4 up to the pixal 10 fold and Tablet)
Price: $599 (~€560)
CPU: Google Tensor G2 (≈ 3.4 k Geekbench multi) – ~2× faster than Murena
GPU: Mali‑G710 MP7 (good for everyday gaming)
RAM/Storage: 8 GB RAM, UFS 3.1
Security: Titan M2 security co‑processor + hardware‑backed keystore, verified boot, attestation
Updates: Monthly security patches, 5 years guaranteed
Pros: Strongest hardware‑rooted security on a consumer phone, pure Android stack (no Google services when using Graphene OS)
Why switch?
Better hardware trust – Titan M2 beats standard boot‑loaders.
Faster updates – stay protected without waiting for LineageOS.
Higher performance – smoother multitasking & AI tasks.
True de‑Googling – Graphene OS runs a clean, auditable Android fork.
💭 If you value privacy and solid performance, the Pixel 7 + Graphene OS is the more compelling upgrade, even at a modest price premium.
#OpenSource #grapheneos #fairphone #degoogle #dataprivacy
@grapheneos @e_foundation 🔗 https://grapheneos.org / https://e.foundation
The FBI raid on the home of Washington Post reporter Hannah Natanson is troubling for a number of reason, but it also demostrated the risks with using biometricsk (fingerprints/face scans) to unlock your device.
Natanson was compelled to unlock a MacBook computer during the search.
Read more about it any why you should avoid biometrics here:
https://decentproject.org/an-fbi-raid-on-a-reporters-home-shows-the-problem-with-biometrics
An FBI raid on a reporter’s home shows the problem with biometrics
<blockquote><p><strong>Quick Look</strong><br/> • The FBI raid on Washington Post reporter’s home shows uncertainty about biometrics under the Fifth Amendment.<br/> • Hannah Natanson was compelled to unlock a MacBook with her fingerprint.<br/> • Until the law is clarified, use PINs/passwords instead of biometrics.</p></blockquote> <p>Recently, the <a href="https://www.theguardian.com/us-news/2026/jan/14/fbi-raid-washington-post-hannah-natanson" target="_blank" rel="nofollow noopener">FBI served a search warrant on the home of Washington Post reporter Hannah Natanson</a>.</p> <p>It's rightfully being <a href="https://firstamendment.mtsu.edu/post/press-freedom-advocates-worry-that-raid-on-washington-post-journalists-home-will-chill-reporting/" target="_blank" rel="nofollow noopener">decried as yet another disturbing attack</a> by the Trump Administration on America's tradition of free and independent press—a tradition that was dealt yet another blow this week when <a href="https://www.npr.org/2026/01/30/nx-s1-5693756/don-lemon-arrest-cnn-minneapolis" target="_blank" rel="nofollow noopener">the Administration arrested four Black journalists in Minnesota</a>, one of whom was former CNN anchor Don Lemon.</p> <p>While much ink has been spilled about the potential chilling effect the raid on Natanson's home may have, some key details of the search are now coming to light.</p> <h3 id="authorities-seized-several-devices-from-natanson-s-home" id="authorities-seized-several-devices-from-natanson-s-home">Authorities seized several devices from Natanson's home</h3> <p><img src="https://i.snap.as/2hatO2Ry.png" alt="Authorities seized several devices from Natanson's home during the January 14th raid"/> <figcaption style="font-style:italic; color:#555;">Authorities seized several devices from Natanson's home during the January 14th raid</figcaption> In court filings, <a href="https://storage.courtlistener.com/recap/gov.uscourts.vaed.588772/gov.uscourts.vaed.588772.35.0_1.pdf" target="_blank" rel="nofollow noopener">the federal government has now detailed</a> the devices seized from Natanson's home, which included two laptops, a cell phone, an audio recorder, a hard drive, and a smartwatch. [...]</p> [SENSITIVE CONTENT]
Quick Look
• The FBI raid on Washington Post reporter’s home shows uncertainty about biometrics under the Fifth Amendment.
• Hannah Natanson was compelled to unlock a MacBook with her fingerprint.
• Until the law is clarified, use PINs/passwords instead of biometrics.
Recently, the FBI served a search warrant on the home of Washington Post reporter Hannah Natanson.
It's rightfully being decried as yet another disturbing attack by the Trump Administration on America's tradition of free and independent press—a tradition that was dealt yet another blow this week when the Administration arrested four Black journalists in Minnesota, one of whom was former CNN anchor Don Lemon.
While much ink has been spilled about the potential chilling effect the raid on Natanson's home may have, some key details of the search are now coming to light.
Authorities seized several devices from Natanson's home

Authorities seized several devices from Natanson's home during the January 14th raid
In court filings, the federal government has now detailed the devices seized from Natanson's home, which included two laptops, a cell phone, an audio recorder, a hard drive, and a smartwatch. While the seizures raise a number of concerns, perhaps overlooked is that Natanson was compelled to unlock one of her MacBook computers using her fingerprint.
Authorities compelled Natanson to unlock a Macbook computer with her fingerprint
It's a remarkable exchange—and one that demonstrates the risks associated with using biometrics instead of PIN numbers or passwords.
Authorities compelled Natanson to unlock her device
The warrant used by authorities to search Natanson's home explicitly stated that agents could compel her to unlock her devices using biometrics, such as a fingerprint or face scan, but they could not compel her to reveal any passwords.

Section of the warrant used to raid Natanson's home (via The Intercept)
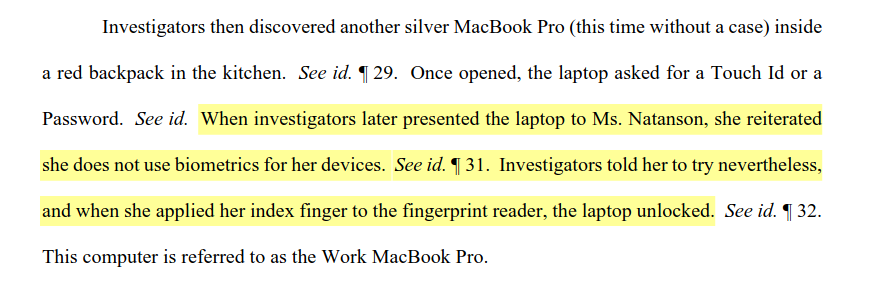
During the search, the government states that Natanson told agents she does not use biometrics and has only one computer and one phone.
Yet, as the search continued, authorities eventually discovered a second computer inside a red backpack in her kitchen.
When agents opened the computer, the lockscreen prompted them to enter a password or use TouchID. The agents then insisted—perhaps against the orders of the search warrant shown above—that she attempt to unlock the device.
The government states that Natanson put her index finger on the scanner, which then unlocked it.
Can you be compelled to unlock your device with biometrics?
This is the exact issue the Decent Project wrote about a little more than two weeks ago.
In our article entitled Should you use biometrics on your phone?, we explored the murky legal landscape over whether law enforcement can compel someone to unlock their device using their fingerprint or face.
Currently, courts are split on the issue. It comes down to whether a court sees the use of biometrics as “testimonial” evidence.
Testimonial evidence is generally anything that requires you to divulge the contents of your mind, i.e. things you know, have seen, or have heard. This kind of evidence has a long tradition of being protected by the Fifth Amendment's privilege against self-incrimination, meaning you cannot be compelled to reveal it.
However, some courts do not think that biometrics are “testimonial” in nature. Instead, they argue a biometric unlock doesn't reveal anything about the content of an individual's thinking or knowledge.
For example, in 2024, the 9th Circuit (in purple above) said in United States v. Payne that biometrics are not afforded the same protections as passwords or PIN numbers:
“While providing law enforcement officers with a combination to a safe or passcode to a phone would require an individual to divulge the 'contents of his own mind,' turning over a key to a safe or a thumb to unlock a phone requires no such mental process.”
We at the Decent Project strongly disagree with this view, and we think Natanson's case is a great example as to why.
What Natanson's fingerprint actually revealed
When Natanson unlocked the MacBook in her kitchen, it revealed several things about her and her relationship to that device.
First, it demonstrated that Natanson knew how to biometrically unlock the device.
This, in our opinion, stands in direct contrast to the 9th Circuit's view that unlocking a device with your finger “requires no ... mental process.”
The government's filing isn't particularly clear on the exact exchange, but when agents “told her to try” to unlock the device and she did so with her index finger, it raises the question: how did she know which finger to use?
Second, her fingerprint demonstrated her control over the computer.
Unlocking a device with your fingerprint is a pretty clear indication that you are the owner of that device, or at least in control of it. If this device is not a shared computer, then it effectively demonstrates that Natanson is responsible for the content found on the device.
It's important to note that Natanson is not a defendant in this case, nor is she a target of the investigation—but in any other context, this kind of evidence could be damning.
Instead, imagine if authorities had found the computer in Natanson's home and it did not have TouchID. Since Natanson cannot be compelled to reveal a PIN or password, what would authorities have to demonstrate that the device is hers?
They could say the device was in her kitchen and that it was found in her backpack, but that's about it.
Takeaway
Not all courts agree with the 9th Circuit when it comes to biometrics. As discussed in our earlier article, the D.C. Circuit Court of Appeals ruled last year that biometrics can be afforded the same protections as other testimonial evidence.
While that's good news, this issue is new and the law is still developing. As such, unless and until there is legal clarity, the Decent Project continues to recommend that individuals do not use biometrics on their devices.
~ Torman
Verify this post: Source | Signature | PGP Key
#privacy #security #OPSEC #FifthAmendment
If you enjoyed reading this or found it informative, please consider subscribing in order to receive posts directly to your inbox:
Also feel free to leave a comment here: Discuss...
RE: https://privacysafe.social/@torman/115996657167176145
Here's the full write-up!
This is all about why the decision to compel a Washington Post reporter to unlock her computer with her fingerprint highlights the risks of using biometrics -- and why you shouldn't.
https://decentproject.org/an-fbi-raid-on-a-reporters-home-shows-the-problem-with-biometrics
#privacy #security #news #OPSEC #FifthAmendment
AodeRelay boostedHoly shit - the government forced Washington Post reporter Hannah Natanson to unlock a Macbook found in her house during a raid of her home.
https://storage.courtlistener.com/recap/gov.uscourts.vaed.588772/gov.uscourts.vaed.588772.35.0_1.pdf
Langeweile am Sonntag? Euch nervt Werbung auf eurem gerät? Dann kommt zum #DiDay nach #Gütersloh ins Klimabüro und verbannt Werbung und Tracking von euren Browsern und Geräten mit den @Datenpunks aus #Bielefeld https://termine.di.day/events/a03c8213-6c38-495d-a0ab-d4c174ec4cd5
Ändere dein Passwort-Tag: Nutzloser Wiedergänger
Jedes Jahr am 1. Februar findet der „Ändere dein Passwort“-Tag statt. Der Tipp ist jedoch ausgelutscht und kontraproduktiv.
Heute ist mal wieder der „Ändere dein Passwort“-Tag. Worauf es wirklich ankommt:
🔹 Jedes Konto braucht ein einzigartiges Passwort.
🔹 Verwende lange, zufällig generierte Passwörter.
🔹 Kein Mensch muss sich die merken – dafür gibt es Passwort-Manager. 👇
🔹 Extra-Schutz? Aktiviere Zwei- oder Mehr-Faktor-Authentifizierung (2FA, MFA).
https://www.kuketz-blog.de/empfehlungsecke/#passwort-manager
#sicherheit #security #password #passwort #keepass #keepassxc #keepassdx
But in order to avoid this complicated mess about whether you can be compelled to provide your biometrics to unlock a device, the best course of action right now seems to be: Don't use them.
It seems clear that PIN/passwords are *not* treated the same as biometrics, and that requiring you to divulge a PIN number is different than demanding your fingerprint/facescan.
https://decentproject.org/should-you-use-biometrics-on-your-phone
The gist is this: It's not clear whether the government can currently force someone to unlock their device with biometrics.
The 9th Cir. (western U.S.) has said that biometrics are not the same as being forced to reveal a PIN/password, and therefore can be compelled.
Hacker Barrel over here tying to scan my network before it will let me order some meatloaf.
Uh...no?
#infosec #security #networking
In March 2026, Kubernetes will retire Ingress NGINX, a piece of critical infrastructure for about half of cloud native environments... Existing deployments will continue to work, so unless you proactively check, you may not know you are affected until you are compromised:
https://kubernetes.io/blog/2026/01/29/ingress-nginx-statement/
WhatsApp migrated 160,000 lines of C++ to Rust to eliminate memory-safety bugs. Here’s how compiler-level security changed its threat model.
More details here: https://ostechnix.com/why-whatsapp-migrated-to-rust-from-c/
"While encryption remains mathematically sound (...) its real-world protections are increasingly bypassed by the privileged position AI systems occupy inside modern user environments."
https://cyberinsider.com/signal-president-warns-ai-agents-are-making-encryption-irrelevant/
Inside the world of men who use smart glasses to secretly film women
https://www.the-independent.com/life-style/smart-glasses-secret-filming-women-b2903950.html
#tech #technology #news #technews #security #privacy #women #meta
There's a lot going on in the United States. If you plan to exercise your legal right to protest, we kindly remind you to not RSVP online, "check in" on a social app, or share your name or email with protest organizers.
Protesting a tyrannical government is core to American culture, and Constitutionally enshrined. You can do so by simply showing up, while maintaining good opsec & data privacy.
#Protest #HumanRights #USpol #USA #SocialMedia #Privacy #Security #PrivacyGuides #DataPrivacyWeek
GrapheneOS version 2026012800 released:
https://grapheneos.org/releases#2026012800
See the linked release notes for a summary of the improvements over the previous release.
Forum discussion thread:
https://discuss.grapheneos.org/d/31269-grapheneos-version-2026012800-released
I've personally grown to hate the security theatre of rotating my bank passwords every six months, especially because of requirements like "must contain one uppercase, one symbol, one lowercase, one special case and the blood of a unicorn."
When mathematically, a simple, grammatically incorrect sentence of 25 characters is much harder for a machine to crack than a gibberish 8-character password with symbols.
Entropy loves length.
I love the idea that the most secure key to your digital life could just be a weird little poem or an inside joke that only you know. Security doesn't have to be painful.
#infosec #passwords #cybersecurity #UX #security #sysadmin #programming #foss #linux #privacy #enshittification #reading #finance
We have spent a decade chasing "frictionless" user experiences, but we forgot that friction is what gives us pause when we need it. New research shows that millions of users are at risk from SMS sign-in links designed to make their lives easier. It turns out, when you send a "magic link" via an unencrypted, legacy protocol like SMS, you aren’t just inviting the user in—you’re inviting anyone who can guess a simple URL string.
The arrogance of modern implementation is breathtaking. We are seeing services that use low-entropy tokens (easily guessed by incrementing a number) and links that never expire. This isn't just a technical glitch; it's a fundamental design failure. We’ve treated the phone number as a digital soul-tether, failing to realize that SMS is effectively a postcard sent through a crowd. If the link is the credential and public, the account is no longer yours.
🧠 Vulnerable tokens: Many services use predictable URL patterns that attackers can brute-force in minutes.
⚡ Eternal sessions: Authentication links frequently fail to expire, leaving personal data exposed for years.
🎓 Massive scale: Over 700 endpoints across 177 services were found leaking sensitive financial and identity data.
🔍 False security: "Possession" of a link is being treated as "identity," bypassing the need for actual passwords.
https://arstechnica.com/security/2026/01/millions-of-people-imperiled-through-sign-in-links-sent-by-sms/
#TechLeadership #CyberSecurity #DigitalIdentity #security #privacy #cloud #infosec #cybersecurity
🇺🇸 America is hurtling toward an AI regulatory "Splinternet," and it isn't coming from overseas; it’s coming from within. As the federal government remains paralyzed by partisan gridlock on nearly every issue, individual states are rushing to fill the vacuum with their own AI mandates. We are witnessing the birth of a legislative patchwork that threatens to turn the American tech landscape into a navigational nightmare for startups and tech giants alike.
It is a fundamental disagreement over who gets to hold the leash on the most transformative technology of our century. When California, Texas, and New York each define "algorithmic bias" or "high-risk models" differently, compliance becomes an impossible burden on progress.
🧠 Regulatory Vacuum: Congressional inaction has forced states to create a chaotic patchwork of conflicting AI laws.
⚡ The Compliance Burden: Smaller AI firms face an existential threat as they struggle to navigate 50 different sets of rules.
🎓 Ideological Divide: The battle lines are drawn between "accelerationists" and "protectionists," with no middle ground in sight.
🔍 Global Stature: This internal friction risks slowing U.S. development while international rivals move toward unified standards.
https://www.technologyreview.com/2026/01/23/1131559/americas-coming-war-over-ai-regulation/
#AIRevolution #TechPolicy #Innovation #ArtificialIntelligence #security #privacy #cloud #infosec #cybersecurity #legislature #laws
Chris( @stoneymonster ) and Elecia( @logicalelegance ) are joined by Mark Omo and James Rowley to talk about safecracking, security, and the ethics of doing a bad job.
Join the chat here: https://embedded.fm/episodes/519
Here’s a tip each from James and Mark:
#security #engineering #embedded #reverseengineering #cybersecurity
Here's the Company That Sold #DHS ICE's Notorious #FaceRecognition App
#Immigration agents have used #MobileFortify to scan the faces of countless people in the US—including many citizens.
#privacy #security #biometrics #ice #dhs
https://www.wired.com/story/mobile-fortify-face-recognition-nec-ice-cbp/
I'm at a celebration of #MLK at the University of Houston.
One of the panelists (sorry, I had to sit in the back, so I don't know who) talked about #risk.
This is in relation to the #redemption that comes from #suffering.
There is #truth in this. I'm old. But the three times I felt something almost #holy was when I risked.
The first time. . .
After my sister changed her major to Women's Studies, she volunteered to be #security at the local #Pride #Parade. I did the training with her. Basically, we were part of a wall of bodies between the parade and the crowd. At one point, there was.a woman yelling and screaming about the Bible, and as I stood in front of her, I didn't even hear her. I felt this deep abiding #calm. I'm not a #believer, but if I were, I would describe it as some kind of divine Presence.
The second time. . .
A coworker was going to the drugstore down the street to get baseball cards, and while I walked down with him, I mentioned that I was treated better at work than at home. He asked me, "What are you going to do about it?" The same calm came to me as I realized I could leave. It was so powerful I went back to work and told my boss that I was feeling weird and I thought I needed to go home. Which I did. I moved in with my sister until I found an apartment.
The third time. . .
I had been working for about thre months when the staffing agency that all of the staff was contracted through wac bought by a bigger agency that mostly staffed the #defense #industry. Instead of #HR, they sent #attorneys. They pulled some shenanigans, but my coworkers in California didn't have to sign #nonCompete #agreements. So they allowed the rest of us to opt out. They even allowed us to jump to a different staffing agency that had profit-sharing. Except the #BigTech we worked for was slow-walkimg the paperwork for the four who were trying to do it. I very carefully set up my remaining PTO and was in another state when my final dey rolled around. Unlike the other four, my role was support. They could survive without me until the paperwork was ready. And, when my boss called and asked if I was not going to work, I felt that calm when I said that I wasn't going to work if I wasn't going to be paid.
In two weeks, all of our paperwork went through, so we all had the same hire date.
As a Greybeard with 25+ years in IT and InfoSec I'd give the following advice to early-career InfoSec folks in a defender role:
Make it a priority to understand, like REALLY understand, the core technologies being used in the environments you are defending. If your environment is primarily Windows then, however distasteful you find it, learn it inside and out. Install it, run it, configure networking, break all of it, and learn how to fix it. The same goes for any OS and for cloud environments, hardware, networking, etc. You can't learn it all instantly but pick a domain with the most impact and start working on it.
There are many situations where this will help you.
1/6
Sicheres Linux: Amutable bringt „kryptografisch verifizierbare Integrität“
Ist das Linux-System sauber? Verifizierbare Integrität soll das sicherstellen. Das Start-up Amutable will das nun umsetzen.
Do Not Use Ring Cameras. Amazon’s Ring cameras are integrated into U.S. law-enforcement workflows. Police agencies can request footage directly, allowing private home surveillance video to be shared with law enforcement.
In 2025, Ring partnered with Flock Safety, further linking consumer cameras to nationwide law-enforcement #surveillance platforms.
#ICE #USPol #Security
https://wiki.icelist.is/index.php/Ring_Cameras_and_Law_Enforcement_Access
Guten Morgen 🌞
#microsoft hat #Bitlocker an den #FBI heimlich weitergegeben. Wer weiß wem noch. Damit ist Microsoft u alle #Software von denen zu benutzen extrem unsicher geworden.
Das Internet ist voll mit dieser Nachricht ➡️ https://duckduckgo.com/?q=microsoft+fbi&t=ffit&ia=web
-
#office #windows #it #news #surveillance #encryption #security
Ireland drafts new surveillance bill expanding police powers to intercept encrypted messages 🔐
Includes legal basis for spyware use & device scanning tech 🕵️♀️
Civil rights groups warn of normalization of extraordinary powers ⚖️
🔗 https://www.theregister.com/2026/01/21/ireland_wants_to_give_police/
#TechNews #Privacy #Surveillance #Spyware #Encryption #HumanRights #Law #Cybersecurity #PoliceTech #CivilLiberties #EU #Government #DataProtection #Security #DigitalRights #Ireland #Irish
There's a saying in crypto: "not your keys; not your coins."
Microsoft again recently showed up why the same goes for encyrption: Not your keys; not your data.
#privacy #security #bigtech #encryption
Read more:
https://decentproject.org/when-encryption-is-not-enough
Did you know that you can use `bastille verify` to check the integrity of your Bastille releases and templates?
> bastille verify 15.0-RELEASE
> bastille verify template/path
This is a great way to ensure that your deployments are
consistent and secure.
On the run up of #DataPrivacyDay we've asked the Tuta Community about your preferred Google alternatives.
Here's what you said about your favorite browsers! 🎉
RE: https://23.social/@thomasfricke/115960624443567139
Wenn Digitale Souveränität jetzt ein Kampfbegriff ist, sind wir jetzt eben im Widerstand.


![[?]](https://i.snap.as/RAHNrslW.png)






