IncusOS – A Platform for Modern Virtualization & Containerization Infrastructure

What is IncusOS?
IncusOS is an immutable operating system created with one clear goal: To run Incus safely, predictably and efficiently. Every part of its design focuses on providing a hardened, consistent and fully automated foundation for container and virtual machine management. Built on Debian 13, IncusOS includes its own kernel and Incus builds to maintain full control over the complete software stack.
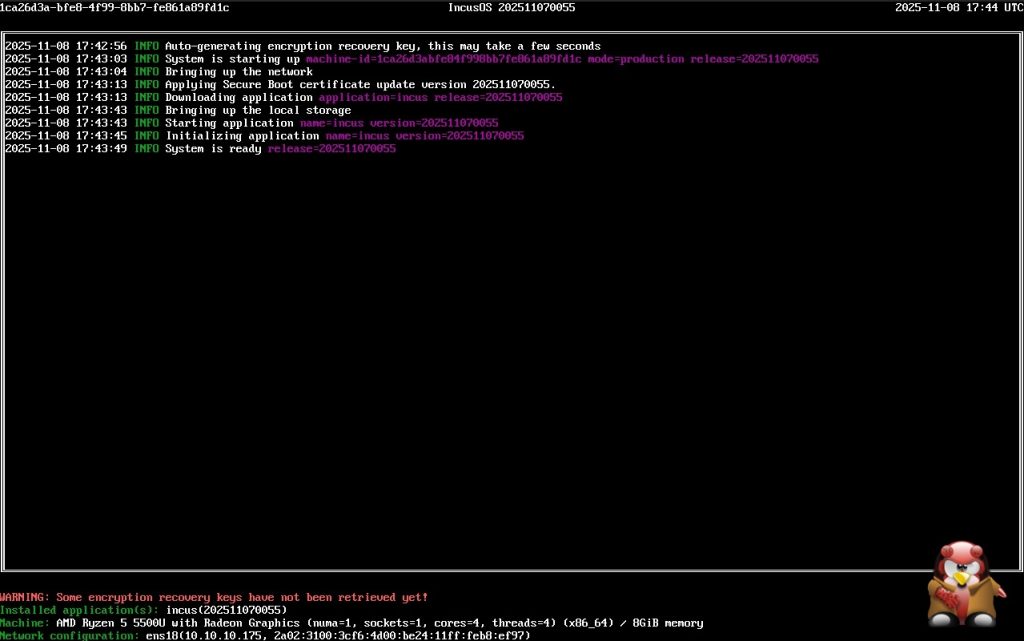
Security and reliability form the core of its architecture. The system uses UEFI Secure Boot and TPM to ensure a verified, tamper-resistant startup and full disk encryption that activates automatically during boot. Updates are handled atomically through an A/B partitioning scheme, allowing the system to roll back instantly if something goes wrong. This approach removes the uncertainty that often comes with traditional update methods.
IncusOS runs in a fully locked-down state. There is no local or remote shell access. Management takes place only through an authenticated REST API, providing a clean, auditable and minimal attack surface. Modern systemd features drive its image builds, secure updates and automate key lifecycle tasks such as first-boot partitioning and TPM-based encryption setup.
In addition to hosting Incus, the system can serve as the base for Operations Center and Migration Manager, tools that simplify large-scale management and make migrations from platforms like VMware straightforward. By enforcing full immutability and ensuring all installations are bit-for-bit identical, IncusOS eliminates configuration drift and guarantees consistent behavior across all servers.
The result is an operating system focused on trust, stability and simplicity. It provides an ideal foundation for anyone building modern, reproducible infrastructure with Incus at its core. Before this, we installed Incus manually on system, crafted clusters and used them for the desired workloads. I already wrote here, how to install and configure Incus and creating an Incus cluster.
Features of IncusOS
IncusOS and Incus comes with many features and one of my key features (espeically compared to Proxmox) is the ARM64 support, which also allows you to easily spawn up VMs on aarch64 hardware architecture but IncusOS comes with a lot more features and many ones are about security and hardening the system. Let’s have a look at them:
Main Design Features
- Boot safety (UEFI Secure Boot and TPM 2.0 measurements)
- Full disk encryption (TPM backed LUKS and ZFS encryption)
- Immutable (A/B partition scheme, all OS partitions read-only and signed)
- Locked down (API only management)
- Designed for modern Intel/AMD or ARM systems
Storage Features
- Automatic local ZFS pool
- Support for complex ZFS pool creation on additional disks
- Fiber Channel & Multipath support
- NVME-over-TCP support
- iSCSI support
- Clustered LVM support (on top of Fiber Channel, NVME-over-TCP or iSCSI)
- Ceph support for software defined storage (Linstor coming soon)
Network Features
- Automatic VLAN-aware bridging making it easy to attach instances to any interface
- Link aggregation support (both passive and negotiated)
- LLDP support
- Support for enterprise proxy servers (including Kerberos authentication)
- Robust NTP support
- Remote logging support through syslog (UDP, TCP, TLS)
- OVS/OVN support for software defined networking
- Native support for Tailscale (Netbird coming soon)
Management Features
- Central management through Operations Center
- Backup/Restore of both the main OS config and individual application data
- Factory reset of either the whole OS or individual applications
- Flexible update management
Trying Incus Online (without any own server)
The Incus project also offers you a possibility to test and try Incus without needed any own server instance running the containers or VMs. This service allows you temporary access to a Linux system running in a virtual-machine hosted on a remote Incus cluster for a limited time and you can simply access it right here.
Creating an IncusOS ISO Image
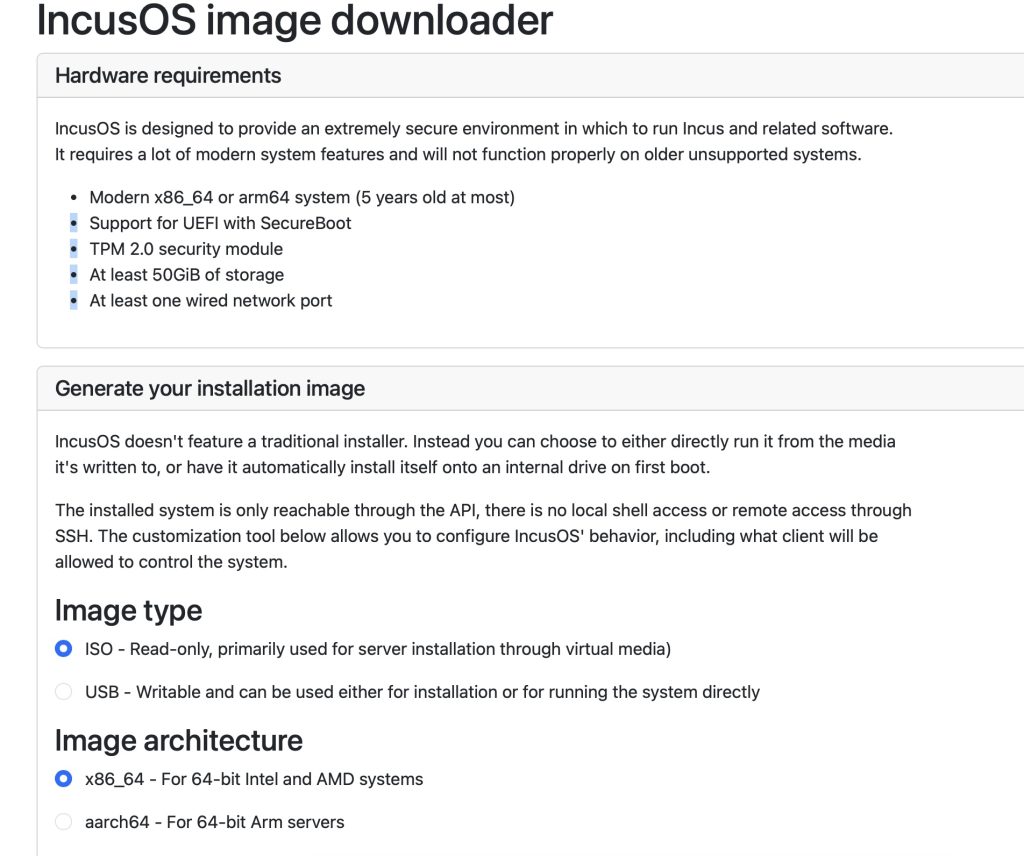
Getting IncusOS is slightly different than usual methods where you can grab your customized installer from the custom installer website which makes it possible to perfectly fit your needs and to avoid creating yourself a custom image. The Incus Customizer works perfectly fine and allows you to create a live bootable ISO, or an ISO to install in your hard drive. IncusOS requires not a lot of resource, just make sure to have a modern x86_64 or arm64 system (no older than five years) with UEFI and Secure Boot support, a TPM 2.0 module, at least 50 GiB of storage, and at least one wired network port present.
Creating an IncusOS image requires you to add your public key of your client(s). Let’s see how this works from scratch on a macOS based system.
Installing Incus Client on macOS
The Incus client on macOS makes it possible to connect directly to remote Incus servers and manage containers, virtual machines, images, and storage from the command line. It offers the same functionality and interface as on Linux, providing a consistent and secure way to control Incus environments without needing a local Incus daemon.
Installation on macOS is simple with Homebrew, the popular package manager for Apple systems. First, make sure Homebrew is installed and up to date by running:
brew update
brew install incusAfter installation, we need to fetch our public key from our client which we need to add to our custom IncusOS customizer:
incus remote get-client-certificate
This command returns our personal public key and must be added and trusted by remote Incus instances. By using the IncusOS customizer, simply drop it in the certificates field and you’re done.
To connect the client to a remote Incus instance, use the following command:
incus remote add my-incus https://incus-node01.lab.gyptazy.com
The client will prompt for trust confirmation if the server certificate is self-signed. Afterwards, you can already start using your IncusOS system from your client. In one of my other blog post, you can also find a how to install and configure Incus and creating an Incus cluster. This way, Incus gets even more interesting by providing secure, immutable images to run your Container and VM workloads.
Conclusion
IncusOS brings together several modern technologies to deliver a platform that prioritizes integrity, safety and simplicity. Each system boots securely with UEFI Secure Boot and TPM 2.0 measurements, ensuring that only verified software is executed from the very first instruction. Full disk encryption, combining TPM-backed LUKS and optional ZFS encryption, protects data at rest without compromising usability or automation.
Every part of the operating system is immutable. The A/B partition scheme allows for atomic updates and instant rollbacks, while all OS partitions remain read-only and cryptographically signed. This design removes the risk of configuration drift and guarantees that each node in a deployment runs exactly the same trusted code.
The entire environment operates in a locked-down state. With no shell access and management provided only through an authenticated REST API, the system maintains a minimal and controlled attack surface. It is purpose-built for modern Intel, AMD and ARM systems, optimized for reliability and consistency across architectures.
This combination of immutability, lockdown and full disk encryption represents a significant advancement compared to traditional Proxmox VE based environments. IncusOS turns the host itself into a secure, verifiable and self-contained platform, providing a stronger foundation for modern infrastructure built on Incus.
