SELinux – How to Create a Policy File
Security-Enhanced Linux (SELinux) is a security module in Linux kernel that provides mandatory access control (MAC) framework for controlling and managing access to various resources within a Linux system. SELinux was developed by the National Security Agency (NSA) and released as open-source software in 2000. Since then, SELinux has become an integral part of many Linux distributions, including Fedora, Red Hat Enterprise Linux, CentOS, and Debian. You may find more information about this within my blogpost here.
The purpose of SELinux is to provide fine-grained access control to system resources such as files, directories, devices, network ports, and system calls. SELinux goes beyond the traditional Unix file permission model and enables administrators to define policies that determine which processes can access which resources. This allows for a more granular level of control over the system and makes it more difficult for attackers to exploit vulnerabilities.
In the past, I often had to create SELinux policy files on my own. Even for Garden Linux I created from scratch the distribution’s gardenlinux-selinux-module.
To build a custom SELinux policy file, you can use the following steps:
- Identify the target application: Determine which application or service you want to create a policy for. This could be a web server, a database application, or any other program running on your Linux system.
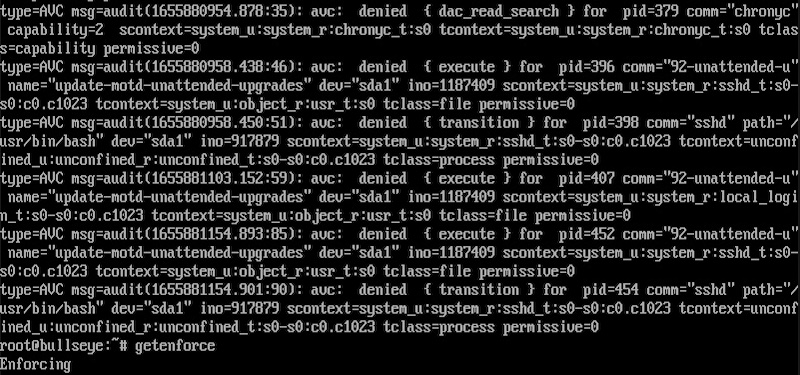
- Generate a SELinux policy module: Use the
audit2allowutility to generate a SELinux policy module based on the audit logs. The audit logs contain information about actions that were denied by SELinux. Theaudit2allowutility can be used to parse the audit logs and generate a policy module that allows the denied actions. - Customize the policy module: Modify the policy module to add additional rules or to restrict certain actions. You can use the
semodulecommand to manage the policy modules and modify their contents. - Compile the policy module: Use the
semodule_packagecommand to compile the policy module into a binary format that can be installed on the system. - Install the policy module: Use the
semodule_packagecommand to install the policy module on the system. This will make the policy module available for use by the SELinux system. - Enable the policy module: Use the
setseboolcommand to enable the policy module for the target application or service. This will ensure that the policy module is enforced by the SELinux system. - Test the policy: Test the policy by running the target application or service and verifying that it is functioning correctly. If the application or service is not functioning correctly, you may need to modify the policy module and recompile it.
Overall, building a custom SELinux policy file can be a complex process that requires a good understanding of the SELinux system and the target application or service. However, by carefully defining the access control rules and labels, you can enhance the security of your Linux system and reduce the risk of security breaches.
